BlueKeep Attacks Arrive, Bearing Cryptomining Malw
Post# of 82692

Exploit Isn't a Worm, But Experts Remain Braced for Mayhem
Jeremy Kirk (jeremy_kirk) • November 4, 2019

BlueKeep Attacks Arrive, Bearing Cryptomining Malware
The cybersecurity community had been holding its breath in anticipation of mass attacks targeting the severe BlueKeep vulnerability in Windows, which Microsoft has patched. The first in-the-wild exploits have now arrived, although experts say they don't constitute an emergency - at least yet.
See Also: Live Webinar | Empowering Your Human Firewall: The Art and Science of Secure Behavior
BlueKeep - aka CVE-2019-0708 - is a vulnerability in Microsoft's remote desktop services, which is a widely used utility for connecting to remote computers. The vulnerability allows an attacker to gain authentication-free access to a machine via RDP by using specially crafted requests (see: 1 Million Windows Devices 'Vulnerable to Remote Desktop Flaw').
Adding to an already bad scenario, attackers could in theory create an exploit with worm-like capabilities, thus infecting a machine and having it hunt for other systems with BlueKeep and automatically infect them too. The risk posed by such a scenario is substantial. Both the U.S. Department of Homeland Security and the National Security Agency have issued alerts to organizations, advising them to immediately patch all systems to eliminate the vulnerability from their IT environment (see: DHS Is Latest to Warn of BlueKeep Vulnerability).
Luckily, the attack code so far seen in the wild isn't a worm, writes U.K. security researcher Kevin Beaumont. But if attackers do create a wormable exploit for the flaw, expect to see wide-ranging consequences.
"If somebody makes a reliable worm for this vulnerability - which to be clear has not happened here - expect global consequences as it will then spread inside internal networks," he writes in a Sunday blog post.
Malware Drop: Monero Miner?
The vulnerability's existence was under wraps until May 14, when Microsoft issued a patch. But as history has shown with the vulnerabilities that led to the WannaCry and NotPetya ransomware - or wiper - malware outbreaks in 2017, issuing a patch isn't enough. Administrators must apply the updates, and organizations' track record for doing so is often spotty (see: Software Bugs: Gotta Catch 'Em All?).
Beaumont writes that he set up honeypots to monitor for BlueKeep exploitation efforts against systems that have port 3389 - used for RDP - exposed. He says his honeypots started crashing on Oct. 23, apparently as a result of attackers' attempts to exploit BlueKeep.
Kevin Beaumont
✔
@GossiTheDog
huh, the EternalPot RDP honeypots have all started BSOD'ing recently. They only expose port 3389.

328
7:40 AM - Nov 2, 2019
Twitter Ads info and privacy
117 people are talking about this
"Over the following weeks, all of the honeypots crashed and rebooted (except one in Australia) with increasing regularity," he writes.
After Microsoft issued its BlueKeep warning, security researchers privately developed exploit code and demonstrated several proof-of-concept attacks, but released no weaponized code. Their decision to avoid publishing proof-of-concept attacks was driven in part by the sheer number of vulnerable machines exposed to the internet - estimated to be as many as 1 million systems at the time the flaw was revealed.
In early September, however, researchers at Rapid 7 released a BlueKeep module for Metasploit, the open-source penetration testing framework. The module could successfully exploit BlueKeep on 64-bit versions of Windows 7 and Windows Server 2008 R2.
BlueKeep affects older versions of Microsoft's OS, including XP, Windows 7, Windows 2003 and Windows Server 2008. But Windows 8 and Windows 10 are immune.
The attack code being delivered by the exploit - as seen by honeypots - does not appear to have any worm-like capabilities. In one instance involving a honeypot in Germany, the exploit delivered what is likely a "coin miner," an application that mines virtual currency, Beaumont writes. A scan on VirusTotal of the file indicated it was first uploaded on Oct. 21 from a Ukrainian IP address, he says.
One honeypot became infected with coin-mining software, according to results from VirusTotal. (Source: Kevin Beaumont)
Many cryptocurrency miners end up being relatively benign, and many attempts to infect systems instead result in the malware just crashing the targeted system, Beaumont says. But of course, these attacks could get worse.
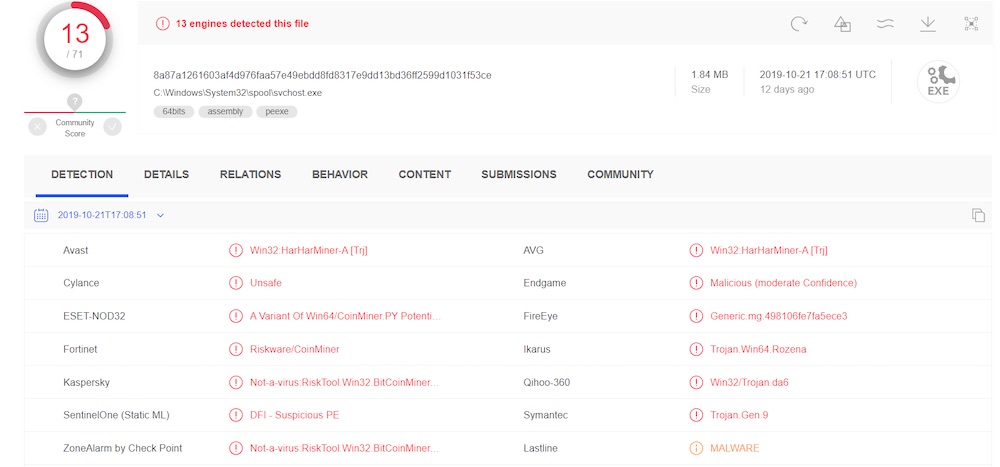
"So far, the content being delivered with BlueKeep appears to be frankly a bit lame - coin miners aren't exactly a big threat," he writes. "However, it is clear people now understand how to execute attacks on random targets, and they are starting to do it. This activity doesn't cause me to worry, but it does cause my spider sense to say 'this will get worse, later.'"
Beaumont says that he shared crash data with security researcher Marcus Hutchins, better known as MalwareTech. Hutchins, who works for Kryptos Logic, famously halted the spread of WannaCry. Hutchins has published a deep technical analysis of the BlueKeep attacks, noting via Twitter that the coin-mining software may be designed to generate monero, a cryptocurrency designed to maintain users' privacy.
MalwareTech
✔
@MalwareTechBlog
It looks like a #BlueKeep worm has finally arrived! Kevin kindly sent me a crash dump and after some investigation I found BlueKeep artifacts in memory and shellcode to drop a Monero Miner. https://twitter.com/GossiTheDog/status/1190654984553205761 …
Kevin Beaumont
✔
@GossiTheDog
huh, the EternalPot RDP honeypots have all started BSOD'ing recently. They only expose port 3389.
View image on Twitter
1,080
12:40 PM - Nov 2, 2019
Twitter Ads info and privacy
521 people are talking about this

724,000 Unpatched Systems Remain at Risk
While there have been plenty of warning about BlueKeep, Beaumont says at least 724,000 internet-connected machines remain unpatched and vulnerable. The figure hasn't changed much since July, he says.
Could indifference be the cause, together with organizations' slow move away from old, outdated Windows operating systems that lack the protections afforded by modern alternatives? "'Only' a few million internet-facing systems were vulnerable before patching, so it does suggest an enormous amount of systems are simply never security-patched," Beaumont writes.
Hutchins theorizes that the detected BlueKeep attacks are likely from a low-level actor who "scanned the internet and opportunistically infected vulnerable hosts using out-of-the-box penetration testing utilities."
While such activity is concerning, it falls short of a worst-case scenario, which would involve attackers indiscriminately scanning for vulnerable ports, Hutchins says. Furthermore, he thinks it's remarkable that BlueKeep took this long to "get detectably weaponized."
But the risks involved in targeting this particular exploit may account for the uncharacteristic delay by attackers. "One might theorize that attackers know they have essentially one shot at using it at scale, and it becomes a game of chicken as to who will do it first," Hutchins says. "It is also worth noting that mass exploitation for gain can be difficult, owing to the risks involved."
 (3)
(3) (2)
(2)Zerify Inc (ZRFY) Stock Research Links
Never argue with stupid people, they will drag you down to their level and then beat you with experience.
Get .... PrivacyLok https://cyberidguard.com/
Try SafeVchat: https://cyberidguard.com/
My comments are only my opinion and are not to be used for investment advice.
Please conduct your own due diligence before choosing to buy or sell any stock.
