Blockchain/Cryptocurrency , Cybercrime , Fraud Man
Post# of 82692
'Graboid' Cryptojacking Worm Spreads Through Containers
Using Docker Containers to Spread Worm Is a New, Untested Technique, Researchers Say
Jeffrey Burt (jburttech) • October 16, 2019

'Graboid' Cryptojacking Worm Spreads Through Containers
Attackers are using Docker containers to spread a cryptojacking worm in a campaign dubbed "Graboid," according to researchers at Palo Alto Network's Unit 42 threat research unit. Although the researchers describe the campaign as "relatively inept," they says it has the potential to become much more dangerous.
Link: https://www.bankinfosecurity.com/graboid-cryp...RQVTdsayJ9
This is the first time the researchers have seen a cryptojacking worm spread through containers in the Docker Engine (Community Edition). While the worm isn't sophisticated in its tactics, techniques or procedures, it can be repurposed by the command-and-control server to run ransomware or other malware, the researchers warn.
The Unit 42 research report did not note how much damage Graboid has caused so far or if the attackers targeted a particular sector.
"If a more potent worm is ever created to take a similar infiltration approach, it could cause much greater damage, so it's imperative for organizations to safeguard their Docker hosts," the Unit 42 report notes.
"Once the [command-and-control] gains a foothold, it can deploy a variety of malware," Jay Chen, senior cloud vulnerability and exploit researcher at Palo Alto Networks, tells Information Security Media Group. "In this specific case, it deployed this worm, but it could have potentially leveraged the same technique to deploy something more detrimental. It's not dependent on the worm's capabilities."
Researchers say that organizations can take several steps to protect containers from attack. Those include ensuring that Docker daemons are not exposed to the internet unless they have a proper authentication method, using Unix socket to communicate with the daemon locally or Secure Shell to connect to a remote daemon, and using firewalls to whitelist incoming traffic.
Targeting Docker Containers and Kubernetes
Containers and the Kubernetes orchestration platform have become key tools for helping enterprises to migrate more of their business to the cloud, so it's not surprising that cybercriminals are turning their attention to them, Chen says.
The Unit 42 researchers note that many endpoint protection solutions don't monitor what's going on inside containers, so intrusions like the Graboid worm are difficult to detect.
About 40,000 Docker container systems and over 20,000 Kubernetes deployments worldwide use default configurations, which is more than 50 percent of all publicly exposed Docker containers, Chen says. The report also states that more than 2,000 Docker engines that are exposed to the internet are insecure, enabling hackers to easily gain full control of both the Docker engine and host.
"The majority of the attacks we have seen on container environments rely on contaminated container images," Chen says. "Many of these images are disguised as other popular container images while containing a backdoor, sometimes retaining the original image's functionality to avoid getting detected. Typosquatting through popular registries such as Docker Hub is one way these images are spread."
Unit 42 and Twistlock Labs, which is also part of Palo Alto Networks, have been finding vulnerabilities in various registries, including in the Docker registry, over the past few years. They have also found that the Kubernetes API has been targeted by bad actors.
Earlier this year, top tech vendors, including Google, Amazon and Red Hat, had to scramble to issue emergency updates to fix a vulnerability that threatened to enable a malicious container to gain root control of a host system.
Graboid Worm
The Graboid campaign involves an automated multistep process, Chen says.
The attackers compromise an unsecured Docker daemon and install a malicious Docker image that is used to communicate with and download malicious scripts from the command-and-control.
Those scripts scout and report back to the command-and-control server about the secured daemons it finds, "almost like sonar bouncing sound off objects and creating a visual of the landscape, except the visual is a list of more than 2,000 vulnerable IPs," Chen says. "From here, the [command-and-control] deploys the cryptojacking malware onto the vulnerable Dockers, as well as the same scripts so it can access and compromise the hosts listed in the IP file. It periodically picks one of the hosts in the IP file to infiltrate. It repeats this indefinitely and it's why it can spread so quickly."
Unit 42 researchers named the Worm Graboid as an homage to the movie "Tremors." The Graboid worm moves in short bursts of speed, like the sandworms in the 1990s movie. (Source: Palo Alto Networks)
The malware downloaded from the command-and-control servers is used to mine for the monero cryptocurrency, look for other vulnerable hosts and randomly pick the next target for the worm, according to the research report. It picks three targets at each iteration: It installs the worm on the first target, stops the miner on the second and starts the miner on the third, creating extremely random mining behavior, researchers say.
In addition, the miner on each infected host is randomly controlled by other infected hosts - for example, other compromised hosts can stop a mining process. Unit 42 researchers are unsure of the reason for this randomized process. It might be to evade detection - though not particularly effective - or to create a self-sustaining system, they write.
"They may have thought that they were being sneaky by having it mine in short bursts to remain under the radar," Chen says. "If too many resources were being used, it could slow or cripple a company's service, which would draw attention. Alternatively, if a Docker [container] was set to automatically scale as load increases, it would begin to spin up new nodes due to the mining from the malware, which a business would likely notice by an increase in their billing, and again expose the malware. Alternatively, it could just be poor design or a reason that we're not aware of."
Unit 42 says it contacted Docker about the Graboid operation and worked with the container company to remove the malicious images.
Canada has the most vulnerable hosts, accounting for 57 percent. The U.S. is next, with about 13 percent, followed by a host of other countries.
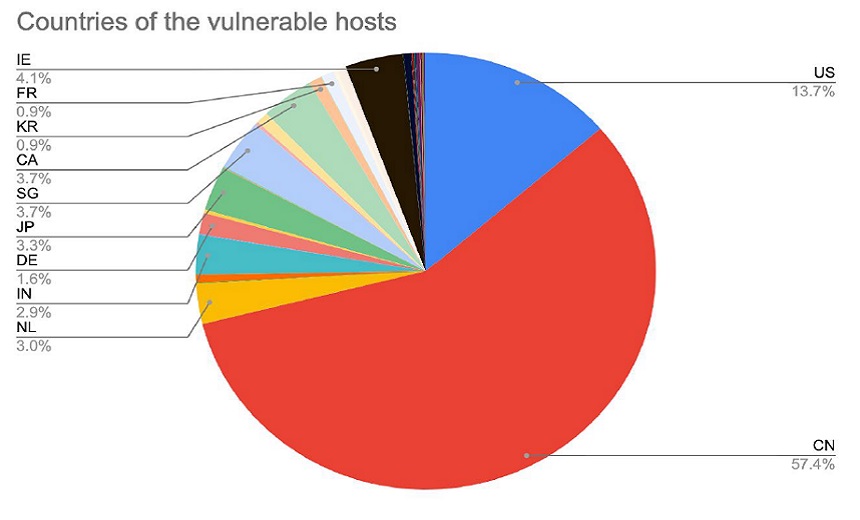
Graboid attacks by country (Source: Palo Alto Networks)
Measuring the Worm
Unit 42 created a Python program to simulate the Graboid worm running over a 30-day campaign, assuming there were 2,000 hosts in the IP file, with 30 percent of them failing during the operation, a 100-second refresh interval and a CPU on each compromised host. The researchers found the worm spread quickly, taking about 60 minutes to reach all 1,400 vulnerable hosts.
"There are, on average, 900 active miners at any time. In other words, the malicious actor owns a 1,400-node mining cluster that has at least 900-CPU mining power," the researchers say. "Because miners on the infected hosts can randomly start and stop, each miner is only active 65 percent of the time and each mining period lasts for only 250 seconds on average."
CryptoDefender protects against CryptoJacking, aren't we glad !!!
 (2)
(2) (1)
(1)Zerify Inc (ZRFY) Stock Research Links
Never argue with stupid people, they will drag you down to their level and then beat you with experience.
Get .... PrivacyLok https://cyberidguard.com/
Try SafeVchat: https://cyberidguard.com/
My comments are only my opinion and are not to be used for investment advice.
Please conduct your own due diligence before choosing to buy or sell any stock.

